All you need to know about irix: The Regional Internet Exchange for Kuching, Sarawak and Borneo.
irix is an internet exchange located at one colocation facility in Kuching. The site is equipped with access devices to enable connections to the irix infrastructure. Colocation services for connected networks are available in the data centre facility, and are offered seperately from the internet services.
The current implementation of the irix peering platform uses an MPLS/VPLS infrastructure. This setup allows for a resilient and highly scalable infrastructure inherent to MPLS, while at the same time the interface towards the members and customers is still the common shared Layer 2 Ethernet platform.
Networks connect with either Gigabit Ethernet (GE), 10 Gigabit Ethernet (10GE), 100 Gigabit Ethernet (100GE) or multiples of these on the access device. All connections are terminated on Extreme SLX routers.
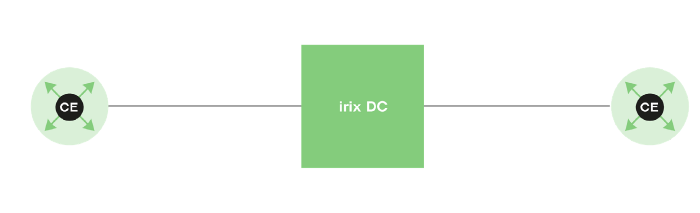
The current irix setup for layer 1 is visualised below.
The greatest danger to any Ethernet network consists of loops. Unless countermeasures are taken, a loop will instantly bring down any L2 network. For example, broadcast frames are looped back to the network, creating duplicates and loading the CPUs of all connected equipment. This, in turn, can lead to a self-sustaining broadcast storm as each broadcast frame is received on all other ports and sent out once again.
irix uses a different technology to combat network loops: Layer 2 access control lists. This feature limits the amount of MAC addresses that can be learned behind a port, and drops frames with any other source MAC address than the original configured one(s).
The irix Connection Agreement allows for connecting one router to a port sold to a member/customer. Only the customer’s MAC address is allowed on the port; no frames with different source MAC addresses are allowed to enter the platform. L2 ACLs prevent several potentially crippling network loops affecting the switching fabric.
If a MAC address change is needed, please be advised that you can replace the existing one, or even temporarily add a second MAC address, via our web portal. We recommend you do that a few hours in advance, so the L2 ACLs can be updated on time. Should you need any assistance or have an emergency, you can always contact irix NOC by email or telephone for immediate resolution.
In addition to port L2 ACLs, irix also implements port flap dampening on all customer facing interfaces. If a port transitions from an Up to a Down state and back more than three times in five seconds, the port is disabled. After ten seconds it is automatically re-enabled.
irix offers high quality interconnection services on a technologically advanced and highly resilient platform supported by a professional organisation. In practice this means we are offering carrier grade service levels. This Quality Statement does not have penalty schemes associated with it.
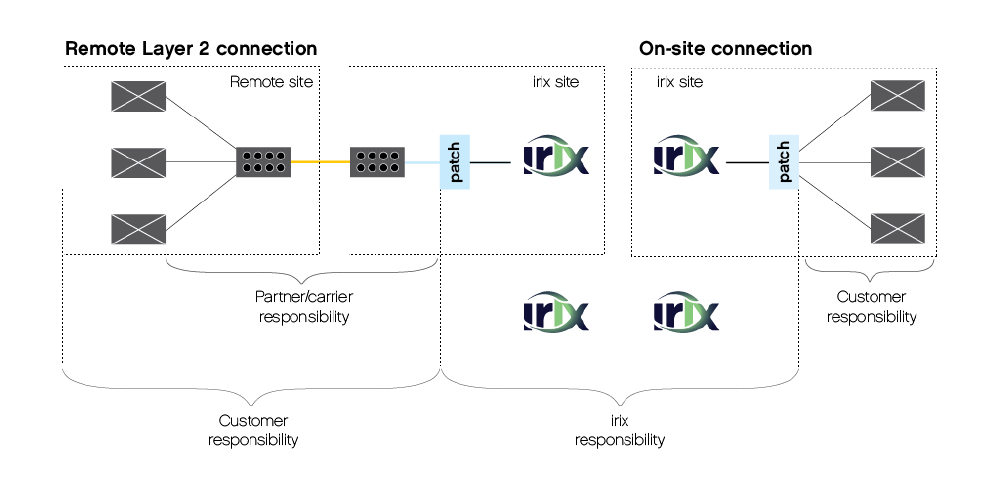
irix is responsible for the correct functioning of its distributed switching infrastructure. The irix service consists of delivering, operating and interconnecting member ports on our switches, including service from these member ports up to and including the local irix patch panel. The customer is responsible for the necessary cabling between the member’s router and the irix switch patch panel through the arrangements made with an irix co-location or, in case of a remote layer-2 connection, arrangements made with a partner/carrier. The customer is always responsible for arranging their own BGP peering with other irix members and for the correct functioning of their own infrastructure, i.e. router equipment.
The initial provisioning of an IXP customer connection (i.e. port on the IXP switching platform) will take a maximum of five (5) working days (Monday-Friday 9.00-18.00 CET).
Upon completion initial provisioning, the port will be placed in the quarantine VLAN. This allows the IXP customer to physically install/configure their router and other equipment at the housing location(s), finalise the cabling arrangements with the colocation or layer-2 service provider and subsequently verify basic (L1/L2 and ping) connectivity to the IXP platform.
Also, this stage of the process allows the irix NOC to verify that the IXP customer’s equipment is configured according to the IXP ‘Allowed Traffic’ rules. Once this is done and the irix NOC has concluded that the interface is ready for production, the interface is placed into the appropriate VLAN.
Connection changes:
- For changes in the configuration without contractual implication, we schedule a provisioning time of 3 working days.
- The customer can always indicate their own envisioned date of delivery of the IXP customer port, which irix will honour as much as possible.
The aim of the irix Network Operations Centre is to have a network availability of at least 99.99%. irix considers both service interruption as well as deterioration of service as service failure.
Excluded from this definition are service failures due to:
- Scheduled maintenance
- Violations of irix regulations by members causing dis-functioning of the exchange
- Force majeure
Service deterioration is defined as not performing according to the set performance parameters outlined below.
Our Network Operations Centre actively monitors the irix infrastructure 24 hours/day, 7 days/week. Problems can be reported to the irix NOC via email or telephone.
When a problem is reported, the irix NOC opens a trouble ticket and assigns an engineer to resolve the problem. The customer is kept up to date of resolution by email. In exceptional cases, e.g. when a customer cannot be reached via email because of the reported network failure, the NOC can agree to keep the customer’s staff up-to-date by phone instead.
In case of service failure (disruption or deterioration) we aim to resolve within 4 hours of reporting. Other issues or requests will be resolved as soon as possible. A ticket will not be closed without the customer’s consent.
In case a customer feels there is a need to escalate a problem, the request is relayed to our Chief Technical Officer.
All trouble tickets can be reviewed through the member portal on the irix website. In many cases, problems are discussed on our tech-l interactive mailing list to which the irix NOC and all customers’ technical contacts are (or can be) subscribed.
All Equipment and Software is maintained and supported by irix. 1st line support is available 24x7 by phone and email, with escalation to 2nd line, if necessary.
Communication with the Technical support is conducted in English.
To ensure the required Quality of Service and facilitate continuous growth, the irix platform is maintained on a day-to-day basis and upgraded regularly. Such upgrades are always carried out during scheduled maintenance windows, between 00:00 and 06:00 local time.
Any scheduled maintenance is announced to the tech-l mailing list with at least 72 hours’ notice.
Scheduled maintenance is the time window during which work is being done to fix or improve the IXP platform, and as a result the platform may not be performing at the usual quality level.
In addition to the above, it may occur that any equipment needs to be replaced immediately, because of hardware or software malfunctioning detected by the irix NOC. In such cases the replacement work may involve so-called Emergency Scheduled Maintenance, which will also be announced to the tech-l mailing list; however, it may not be announced well in advance. This, of course, is due to the immediate nature of the required repair activity and is always up to the discretion of the irix technical team.
Allowed Traffic Types on Unicast Peering LANs.
Important: The irix NOC reserves the right to disable ports that violate the rules below.
To ensure smooth operation of the irix infrastructure we impose a set of restrictions on what kind of traffic is allowed on the peering fabric. This page gives a summary of those restrictions. For more info, including hints on how to configure equipment, please see the irix Configuration Guide.
Ethernet framing
The irix infrastructure is based on the Ethernet II (or “DIX Ethernet”) standard. This means that LLC/SNAP encapsulation (802.2) is not permitted. For more information on the differences, see the Ethernet FAQ, question 4.1.2.2 Ethernet typesFrames forwarded to irix ports must have one of the following ethertypes:
- 0x0800 - IPv4
- 0x0806 - ARP
- 0x86dd - IPv6
One MAC address per connection
Frames forwarded to an individual irix port shall all have the same source MAC address.
No proxy ARP
Use of proxy ARP on the router’s interface to the Exchange is not allowed.
Unicast only
Frames forwarded to irix ports shall not be addressed to a multicast or broadcast MAC destination address except as follows:
- broadcast ARP packets
- multicast ICMPv6 Neighbour Discovery, Neighbour Solicitation, and MLD packets. Please note that this does not include Router Solicitation or Advertisement packets.
No link-local traffic
Traffic related to link-local protocols shall not be forwarded to irix ports. Link-local protocols include, but are not limited to, the following list:
- IRDP
- ICMP redirects
- IEEE 802 Spanning Tree
Vendor proprietary protocols. These include, but are not limited to:
- Discovery protocols: CDP, EDP, LLDP etc.
- VLAN/trunking protocols: VTP, DTP
- Interior routing protocol broadcasts (e.g. OSPF, ISIS, IGRP, EIGRP)
- BOOTP/DHCP
- PIM-SM
- PIM-DM
- DVMRP
- ICMPv6 ND-RA
- UDLD
- L2 Keepalives
The following link-local protocols are exceptions and are allowed:
- ARP
- IPv6 ND
No directed broadcast
IP packets addressed to irix peering LAN’s directed broadcast address shall not be automatically forwarded to irix ports.
No-export of irix peering LAN
IP address space assigned to irix Peering LANs must not be advertised to other networks without explicit permission of irix.
Using Application layer protocols to unleash malicious actions against other irix customers over irix infrastructure, is forbidden. irix reserves the right to disable a customer’s port in case of complaints of attacks/abuse originating from such customers. The following list includes, but not limited to, some very well-known attacks that we forbid:
- BGP hijacking
- DNS amplification/flood
- HTTP flood
- NTP amplification
- UDP flood
- ICMP flood
- Simple Service Discovery Protocol (SSDP)
Did you experience or notice a customer abusing their irix connection for malicious actions?
Contact Us →
Please get in touch to file a complaint providing information about:
- The timestamp of the event
- The type of the event
- The related prefixes/ASNs
- The parties involved
- Any other relevant information providing appropriate context.
Typically, this information can be found in (but is not limited to) router logs, syslog servers, packet captures, BGP monitoring services.
irix will investigate to confirm the complaint and take appropriate action.
